Authors: Cisco ASA - CVE-2016-6366A vulnerability in the Simple Network Management Protocol (SNMP) code of Cisco Adaptive Security Appliance (ASA) Software could allow an authenticated, remote attacker to cause a reload of the affected system or to remotely execute code.The vulnerability is due to a buffer overflow in the affected code area. The vulnerability affects all versions of SNMP (versions 1, 2c, and 3) when enabled on a virtual or physical Cisco ASA device. An attacker could exploit this vulnerability by sending crafted SNMP packets to an SNMP-enabled interface on the affected system.
An exploit could allow the attacker to execute arbitrary code and obtain full control of the system or to cause a reload of the affected system. The attacker must know the SNMP community string to exploit this vulnerability.Note: Only traffic directed to the affected system can be used to exploit this vulnerability. This vulnerability affects systems configured in routed and transparent firewall mode only and in single or multiple context mode. This vulnerability can be triggered by IPv4 traffic only.
The attacker requires knowledge of the configured SNMP community string in SNMP version 1 and SNMP version 2c or a valid username and password for SNMP version 3.Cisco has released software updates that address this vulnerability. Mitigations are listed in the Workarounds section of this advisory. How to login in Cisco ASA?If you known nothing about the Cisco ASA device, please try to discovery something useful with or custom tools/methods.If snmp is enabled, we can try to crack the password with metasploit. Msf auxiliary(snmplogin) set PASSWORD publicPASSWORD = publicmsf auxiliary(snmplogin) set RHOSTS 192.168.206.114RHOSTS = 192.168.206.114msf auxiliary(snmplogin) run+ 192.168.206.114:161 - LOGIN SUCCESSFUL: public (Access level: read-write); Proof (sysDescr.0): Cisco Adaptive Security Appliance Version 9.2(1). Scanned 1 of 1 hosts (100% complete). Auxiliary module execution completedNow, CVE-2016-6366 can help us exploit remote cisco device.
Cisco's Adaptive Security Device Manager (ASDM) is the GUI tool used to manage the Cisco ASA security appliances. In this blog I'll reveal to you some of my favorite tips, tricks and secrets found inside ASDM. If you haven't dealt with it before, ASDM is a free configuration, monitoring and troubleshooting management tool that comes with the ASA. In a nutshell, ASDM will manage all the features of the ASA appliance including FW, IPS and VPN.
Unlike its big brother Cisco Security Manager (CSM), ASDM is made to configure a standalone ASA one at a time. CSM is the tool you would use to manage and share policy across multiple ASA's, routers, and IPS appliances.First, installing the tool. You can download ASDM from cisco.com or from your ASA itself. You can then run it inside a browser or download the ASDM launcher so it runs as its own application on your PC. I highly recommend ASDM launcher as the way to go. The ASDM launcher works for both Windows and MAC OSX (requires ASDM version 6.4.5 or later). Once launched it will look like the below image.
You fill out the info and away you go.A few secrets about ASDM launcher. First, to get the MAC launcher working you must install it directly from your ASA using a web browser. Currently, there is not a downloadable.dmg file on cisco.com, only a.msi file for windows.Second, you see that cool 'run in demo mode' checkbox? This can be a very handy feature and is available to everyone. To enable it, check the box and click on the link it provides. This will take you to cisco.com where you will need to download the ASDM demo.msi package.Once installed, ASDM can then be used in a offline demo mode on a windows or mac computer. Demo mode provides you with several configuration types to choose from so you can make it pretend to be an ASA FW or a ASA FW with IPS or a ASA with SSLVPN, etc.
The ASDM demo mode even models event logs. All in all ASDM demo mode gives you the experience of configuring and monitoring a live ASA.Which brings me to another ASDM secret, demo mode is designed for windows but will also work on MACs. This is not something supported by Cisco or found in there docs. It is more of a hack, but a useful one for those (like me) that don't like to run fusion on their MACs.
Here is how you get it to work on a MAC running Lion:-First, On your MAC install the ASDM launcher by connecting to an ASA via a web browser and clicking install launcher. -Second, download and install ASDM demo.msi on a Windows PC.-Next, Copy the Demo folder contents from C:Program FilesCisco SystemsASDM to your MAC.-On your MAC, open the folder the launcher app is in (usually applicationsCisco) and right click on the launcher app. Now click show package contents-A new finder window will open. Navigate to /Applications/ASDM/Cisco ASDM-IDM.app/Contents/Resources/Java/demo-Finally, copy the contents of the windows demo folder into this folder. Now Mac launcher demo should work great!Now that we have ASDM installed here are some quick tips. Need to see if there are upgrades for your specific ASA type and version?
Use the check for updates tool in ASDM. This software update wizard is much quicker and error free than going to cisco's website downloading the images then uploading them to the ASA and configuring it to use them. This can all now be done with about 4 clicks right from ASDM. Huge timesaver!. Need to quickly see in/out throughput on ASA interfaces? On homepage click on an interface and below it will show the input and output kbps.
Need to quickly see your VPN sessions and their details? On homepage view the VPN sessions and click on details to see all the info about your sessions. Packet Tracer is a must use tool for ASA admins. If you haven't heard about it yet see my previous blog. Packet tracer lets you model how the ASA will react to certain traffic types moving through it. The new feature you need to know about is now tracer can model traffic based on usernames and FQDNs. Need to send an alert message to your clientless sslvpn users?
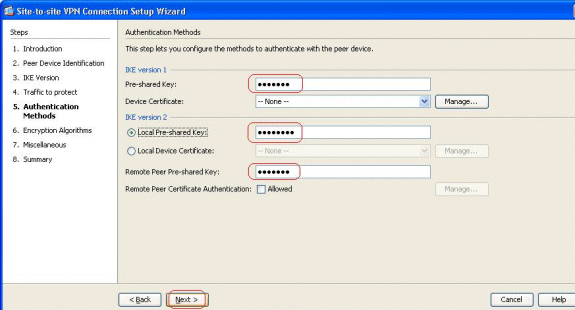
Under tools you'll find just such a feature. You can send any alert message you want to your users. Need to get your ASA configured fast? Need to capture packets off the ASA quickly? Use the ASDM wizards! They save you time and eliminate common mistakes, especially for VPN setup.
In this case wizards are not for dummies.Can't find where in ASDM to configure something? Find it quickly using the look for tool. You can find it on the ASDM toolbar. Just type in a keyword or two of what you are looking for and the ASDM assistant will take you there. To speed up firewall rule creation use the drag and drop of objects. You can quickly drag and drop objects and service objects into your firewall rule table.
If the object table is not open goto view/services to open it. Need to find where an object is being used? Right click on the object and select where used. Need to put in a temporary rule that auto-expires after a certain time? Or maybe a rule that expires and only allows traffic during business hours for contractors? Use the time-based option in your firewall rules under advanced options on a rule. Need to quickly add NAT to a server or any host object?
Use the new object based NAT. This can be a huge timesaver. Need to find botnet and other malware activity quickly?
Cisco Asa 5505 Router
Turn on the botnet traffic filter license on your ASA and you'll see all sorts of useful info on malicious traffic. Think you might have a slow or broken connection to your authentication server? You can quickly check the server to ASA performance from your ASDM monitoring/properties/aaa server view. Great tool to help troubleshoot authentication slowness or other erradic behavior.Need to see who is currently logged in to manage the ASA? Need to kick them off? You can do both from the Monitoring Properties Device Access ASDM/HTTPS/Telnet/SSH Sessions screen.Need to troubleshoot the ASA connections?
Need to parse the ASA logs real-time? The ASDM Log viewer under monitoring is a nice tool for just such activities. It is best suited to near or real-time log parsing. A few of the really cool tools are create rule, show rule, whois and dns lookup. Any of these can be accessed by right clicking on a log message. Again can be a big timesaver.Well, there are some of my favorite ASDM tips.
Cisco 5505 Asa
If you have some of your own to share please post them. If you have any questions let me know.The opinions and information presented here are my PERSONAL views and not those of my employer. I am in no way an official spokesperson for my employer.More from Jamey Heary: for more articles on security.